According to the FBI’s advisory, Ragnar Locker ransomware operators have targeted ten different sectors including energy, manufacturing, government, information tech, finance, etc.
On Monday, the Federal Bureau of Investigation (FBI) released a FLASH advisory disclosing that the Ragnar Locker ransomware gang has targeted at least 52 critical infrastructure organizations in America as of January 2022.
Ten Different Sectors Targeted
According to the FBI’s advisory, Ragnar Locker ransomware operators have targeted ten different sectors. These include energy, manufacturing, government, information tech, finance, etc. However, the agency didn’t release details of the impacted entities. It is speculated that one of the targeted organizations was the high-profile firm Capcom and the attack affected around half a million individuals.
About Ragnar Locker Ransomware Gang
The infamous group came under the FBI’s radar in April 2020 when the gang influenced the attack tactics of other ransomware groups like Maze. The gang also joined a ransomware cartel with SunCrypt, Maze, LockBit, and Conti.
The FBI explained that the Ragnar Locker gang excels in double extortion techniques. The attackers steal data, encrypt the compromised systems, and threaten their victims to leak the stolen files if they refuse to pay the ransom.
Ragnar Locker Gang’s Attack Tactics
According to cyber security researchers, the Ragnar Locker ransomware gang uses a specially designed virtual machine image to execute payload while evading anti-malware detection. Moreover, the gang uses the Salsa20 encryption algorithm and RSA-2048 to encrypt file keys and obtains privilege escalation through COM objects by exploiting the CVE-2017-0213 vulnerability.
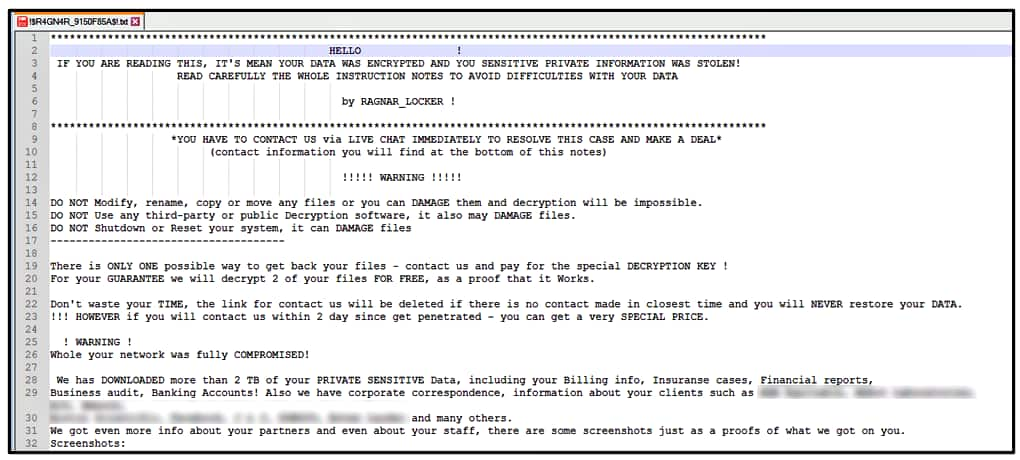
More Ragnar Locker Ransomware Attacks
- Ragnar Locker ransomware hits Capcom Gaming details leaked
- Ragnar Locker ransomware gang using Facebook ads to extort victims
- Ragnar Locker ransomware gang steal 10 TB of data from energy giant
Critical Infrastructure Orgs under Threat
In the past few years, critical infrastructure organizations have become a key target of choice for ransomware operators. The attack on Colonial Pipeline and many other high-profile firms validate the claim that threat actors are increasingly targeting these organizations because of their operational significance as they can’t afford downtown and usually give in to the attackers’ demand.
Do Not Pay the Ransom
The FBI urges organizations and victims to report ransomware attacks immediately to their local field office rather than paying the ransom to “criminal actors.” Before taking such decisions, executives should weigh all available options to “protect their shareholders, employees, and customers.”
Credit: Source link





















