Netskope released a research highlighting the continued growth of malware and other malicious payloads delivered by cloud applications. The year-over-year analysis identifies the top trends in cloud attacker activities and cloud data risks from 2021 as compared to 2020, and examines changes in the malware landscape throughout 2021, highlighting that attackers are achieving more success delivering malware payloads to their victims and offering advice for improving security posture in 2022.
The research showed that more than two-thirds of malware downloads came from cloud apps in 2021 and identified Google Drive as the app with the most malware downloads, taking the spot from Microsoft OneDrive. The research also uncovered an increase in malicious Office documents from 19% to 37% of all malware downloads, all pointing to a rise in cloud application security risks. The report further shows that more than half of all managed cloud app instances are targeted by credential attacks.
As the workforce becomes more distributed and stretches the limits of network and data security, organizations must apply modern security controls, such as Security Service Edge (SSE)-led architectures, to enable users the freedom to securely move about the cloud.
The prevalence of malware delivered by cloud applications
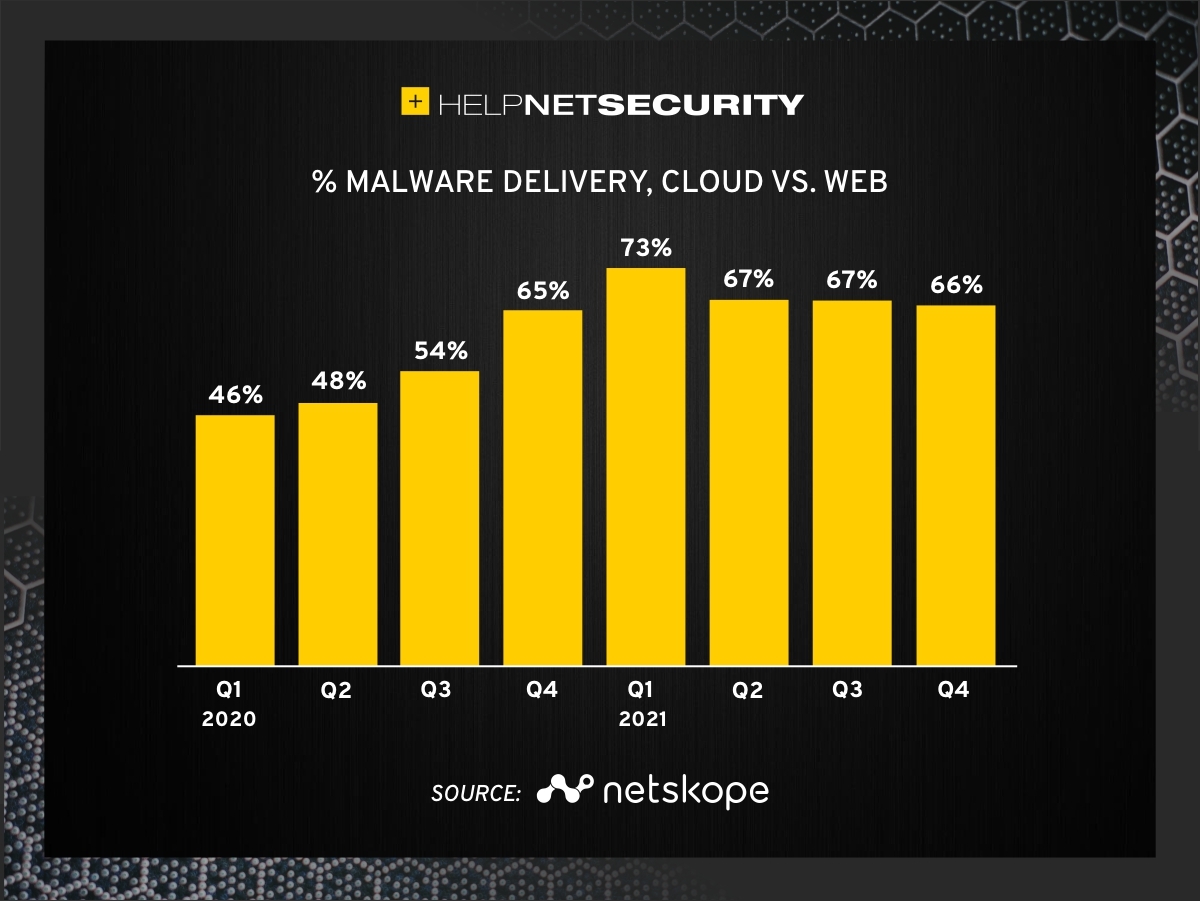
- Cloud-delivered malware is now more prevalent than web-delivered malware. In 2021, malware downloads originating from cloud apps increased to 66% of all malware downloads when compared to traditional websites, up from 46% at the beginning of 2020.
- Google Drive emerges as the top app for most malware downloads. Research found that Google Drive now accounts for the most malware downloads in 2021, taking over the top spot from Microsoft OneDrive.
- Cloud-delivered malware via Microsoft Office nearly doubled from 2020 to 2021. Malicious Microsoft Office documents increased to 37% of all malware downloads at the end of 2021 compared to 19% at the beginning of 2020, as attackers continue to use weaponized Office Documents to gain an initial foothold on target systems. The Emotet malspam campaign in Q2 2020 kicked off a spike in malicious Microsoft Office documents that copycat attackers have sustained over the past six quarters, with no signs of slowing down.
- More than half of managed cloud app instances are targeted by credential attacks. Attackers constantly try common passwords and leaked credentials from other services to gain access to sensitive information stored in cloud apps. While the overall level of attacks remained consistent, the sources of the attacks shifted significantly, with 98% of attacks coming from new IP addresses.
- Corporate data exfiltration is on the rise. One out of seven employees takes data with them when they leave their employer, using personal app instances. Between 2020 and 2021, an average of 29% of departing employees downloaded more files from managed corporate app instances, and 15% of users uploaded more files to personal app instances in their final 30 days.
“The increasing popularity of cloud apps has given rise to three types of abuse described in this report: attackers trying to gain access to victim cloud apps, attackers abusing cloud apps to deliver malware, and insiders using cloud apps for data exfiltration,” said Ray Canzanese, Threat Research Director, Netskope Threat Labs.
“The report serves as a reminder that the same apps that you use for legitimate purposes will be attacked and abused. Locking down cloud apps can help to prevent attackers from infiltrating them, while scanning for incoming threats and outgoing data can help block malware downloads and data exfiltration.”
Credit: Source link