The vulnerability in WinRAR trialware could be abused by a remote attacker for executing arbitrary code on any system thus, getting an opportunity to launch a range of attacks.
According to a report from Positive Technologies, a remote code execution vulnerability was identified in a free trial version of WinRAR. The vulnerability was discovered in the software’s trialware file archiver utility.
SEE: Hackers are using 19-year-old WinRAR bug to install nasty malware
In a technical writeup, Igor Sak-Sakovskiy from Positive Technologies wrote that the bug can be exploited “to achieve remote code execution (RCE) on a victim’s computer.” On June 14, 2021, the issue was addressed with the release of WinRAR v. 6.02.
About WinRAR Trialware
WinRAR has a free trial license before users can buy an actual license for the software. Windows Explorer doesn’t display this trial version’s compression format (.rar archive). Therefore, WinRAR is commonly used by those who work with this format or have to download a .rar archive for once to open a utility.
How the Bug was Exploited
Research conducted by the infosec firm revealed that the vulnerability in WinRAR trialware could be abused by a remote attacker for executing arbitrary code on any system thus, getting an opportunity to launch a range of attacks.
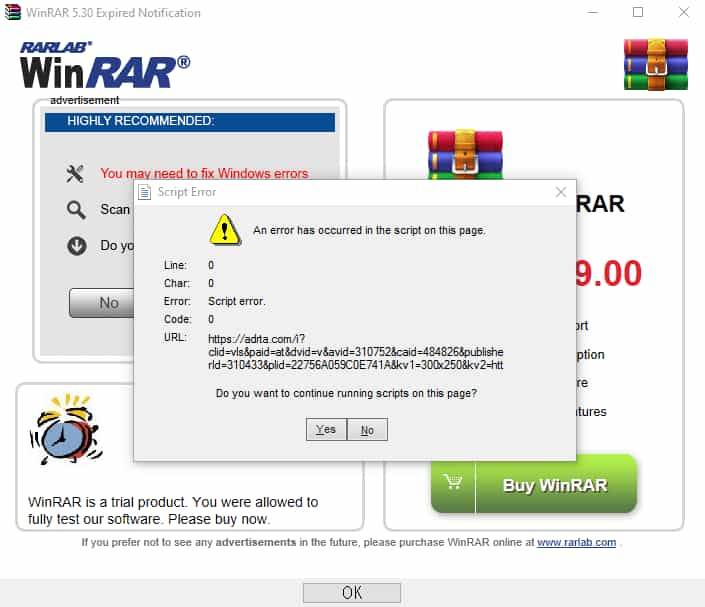
Error that indicates WebBrowser JS parser inside of WinRAR (Image: PT Security)
An attacker could modify/intercept requests sent to the app user and introduce RCE via a WinRAR dialogue box that can spawn an Internet Explorer instance. This window utilizes “mshtml.dll implementation for Borland C++.” This is the same language in which WinRAR is written.
Furthermore, blog post published by researchers revealed that they could identify and modify the dialogue box’s traffic by sniffing WinRAR traffic with Burp Site. If the dialogue box received an HTTP 301 response, it would follow that as it indicates a permanent redirect from WinRAR’s servers. Hence, researchers could send it wherever they wanted to after injecting their own content into the box.
SEE: WinRar and TrueCrypt Installer Dropping Malware on Users’ PCs
Moreover, fake ARP (address resolution protocol) packets were sent to the dialogue box from a hostile domain. Researchers could retrieve localhost information and run apps such as Windows Calculator. Researchers noted that Word files, PDFs, .rar archives, and Python scripts could be opened without further warnings.
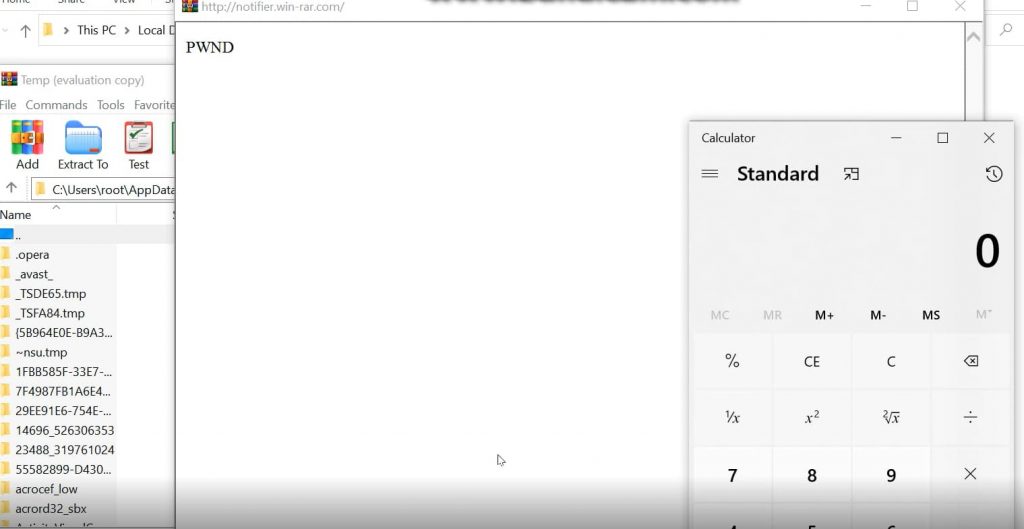
Successful execution of the calculator application in Windows (Image: PT Security)
Flaw Has Been Patched
It is tracked as CVE-2021-35052 and impacts the software version running 5.70. This version was released 2 years ago and has since been superseded by other versions. Regarding the exploitation of the bug that has been patched already, WinRAR released this statement.
“Such attacks are only possible if the intruder has managed to spoof or otherwise control user’s DNS records.”
However, we cannot ignore that people tend to use free software for a long time, even after its due date has passed. Therefore, REC vulnerabilities must be taken seriously and handled with a sense of urgency since the risk it poses is quite significant.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.
Credit: Source link





















