A new report reveals that since the Russian attack on Ukraine, Anonymous and its affiliate groups have compromised 90% of misconfigured cloud databases owned by different Russian organizations.
As you may already know that Russia has come under the radar of hacktivists, particularly the Anonymous collective, after the country invaded Ukrainian territories on February 24th, 2022. Since then, Russian IT infrastructure is being targeted every other day including government websites, State-run TV channels, online video streaming platforms, etc.
But now, researchers have revealed that hackers launched a large-scale cyberattack on misconfigured and exposed cloud databases owned by different Russian organizations. The severity of the attack can be quantified by the fact that around 90% of these databases have been compromised by hackers.
Details of the Breach
According to the IT security researchers at Website Planet, Anonymous and its affiliate group of hackers compromised around 90% of Russian cloud databases that were exposed to the public without any security authentication or password.
Although there is no clarity over whether the data was downloaded or not and what the hackers intend to do with it chances are bright that they might use it for additional attacks.
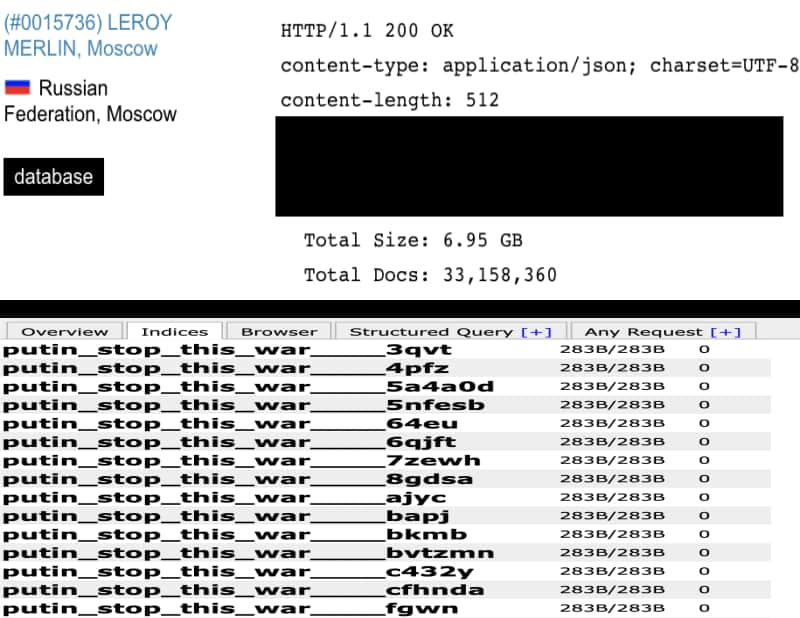
According to Jeremiah Fowler of Security Discovery who collaborated with Website Planet to complied this report, out of Russia’s 100 exposed cloud databases that they discovered through different tools and sources, at least 92 were compromised.
In most cases, attackers fully erased the dataset with a MeowBot-inspired script. One of these databases belonged to the CIS (Commonwealth of Independent States). Also, part of the compromised information was a dataset belonging to Russian ISP Green Dot that contained a large number of secret keys having mail.ru as the host server.
Files Renamed with Pro-Ukraine Messages
Fowler further revealed that the files stored in the compromised databases were either removed or renamed with pro-Ukrainian messages, most of which read:
“Putin stop this war,” “no war,” and “HackedByUkraine.”
Apart from the hack, the database may have exposed weak administrative credentials and emails, making employees potential targets of social engineering attacks to “gain access deeper in the organization of social engineering,” Fowler noted.
Identifying unsecured databases isn’t as a big deal as it seems. With only a few taps, search engines like Shodan or Censys can constantly scan the internet and open databases with default logins effortlessly.
However, the fact that hackers are using these databases for hacktivism is something never seen before. Nevertheless, researchers warn that as an unsuspected user one should keep an eye on their data whether it is involved in a data breach or left exposed due to misconfigured databases.
What is MeowBot or Meow attack?
A MeowBot or Meow attack is a type of attack in which the bot searches for unsecured databases and deletes them entirely without any explanation. Previously, UFO VPN had its database compromised and wiped out by MeowBot.
What happens in database misconfiguration?
A misconfiguration occurs when an administrator or company leaves their database open to public access without any password or security authentication. These databases are easy to access through different search engines and often store a massive trove of sensitive and personal data.
As of July 2020, 9,517 unsecured databases were identified with more than 10 billion records globally. At that time, 51% of the databases were exposed on Elasticsearch while 49% were on MongoDB.
Credit: Source link



