So far, Microsoft has informed 140 companies about the new attack campaign being carried out by Nobelium 14 of which were compromised by the group.
The IT security researchers at Microsoft have revealed that the threat actors from the Nobelium group are back in action and currently targeting resellers and Cloud service providers.
Nobelium is the same group that launched the massively devastating supply chain attacks against Texas-based SolarWinds’ Orion software last year. the infamous group is also known for using SUNBURST and TEARDROP malware.
Microsoft has been following the activities of this group quite closely since then and just last month, the company warned of Nobelium’s comeback after the actors were found using a never-before-seen post-exploitation backdoor called FoggyWeb.
The backdoor is capable of stealing sensitive data from a compromised AD FS (Active Directory Federation Services) server. For your information, according to the U.S. government and other authorities Nobelium is part of Russia’s foreign intelligence service known as the SVR.
140 service providers informed; 14 compromised
In the latest blog post, Microsoft’s Corporate Vice President, Customer Security & Trust, Tom Burt revealed that since May 2021, the company has informed 140 resellers and technology service providers about Nobelium’s cyberattacks on their critical infrastructure.
However, since Microsoft is still investigating, Mr. Burt revealed that 14 of the informed companies were compromised by the group. It is worth noting, the prime target of this campaign are resellers and technology service providers who specialize in managing, customizing, deploying cloud services and other technologies on behalf of their customers.
We believe Nobelium ultimately hopes to piggyback on any direct access that resellers may have to their customers’ IT systems and more easily impersonate an organization’s trusted technology partner to gain access to their downstream customers, Mr. Burt noted in his blog post.
Nobelium’s previous attack on SolarWinds involved exploiting critical vulnerabilities (the group also hacked iPhones by exploiting iOS 0-day flaws) but in the latest attack, the group’s modus operandi involves phishing and password spraying attack.
This indicates that the group is keeping its strategy plain and simple by using social engineering tactics to steal valid credentials and gain privileged access.
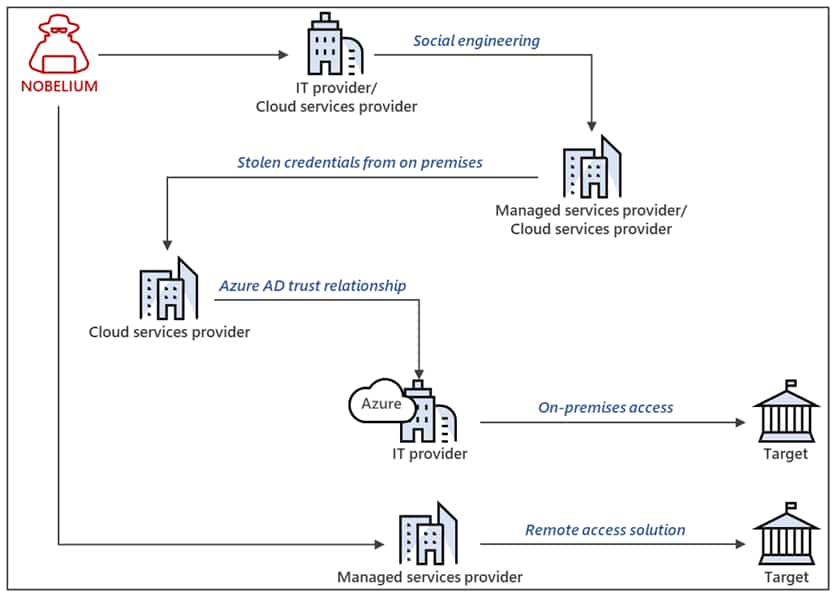
Example intrusion conducted by NOBELIUM (Microsoft)
What is Password Spraying Attack?
In this kind of attack, threat actors try to brute-force accounts cycling the same passwords on multiple accounts at once. This helps them hide failed attempts using different IP addresses and evade automated defenses such as IP blocking or password lockout designed to block multiple failed login attempts.
Microsoft’s technical guidance
Microsoft’s Threat Intelligence Center (MSTIC) has also released technical guidance for companies and downstream customers to protect themselves against cyberattacks from Nobelium.
Protection against phishing attacks
From small businesses to large corporations, providing adequate education about phishing and cybersecurity is a must. However, for beginners, using common sense can help in the long run therefore, refrain from opening anonymous emails and do not click links or download attachments from them.
Nevertheless, teach employees how to spot phishing attempts by simply following these steps:
- Phishing attempts almost always contain a link, downloadable attachment, or directive telling people to do something ASAP.
- There are often a lot of spelling mistakes, but not always.
- The email or message can instill a sense of urgency to get people to act quickly without thinking.
- It may be a threat or even blackmail, as is the case with sextortion phishing scams.
- The email signature will usually look strange or different from normal.
- Despite all of the common telltale signs, phishing emails can look legitimate. Hackers can make spear phishing attacks that look like a known company, bank, or contractor sent the email. However, employees should use common sense to think about whether this email was warranted. Does it contain a link and is asking them to log onto their account for no reason? Most banks, for example, won’t send an email asking people to log into their accounts or send any links.
- Phishing emails or messages aren’t always from strangers. Sometimes they’re sent from the compromised accounts of friends, coworkers, or other contacts.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.
Credit: Source link



















