In the rapidly advancing digital landscape, cybersecurity is at the forefront of ensuring the safety and integrity of personal and organizational data. One of the most debated aspects of modern cybersecurity is the role of biometrics—a technology that uses unique human characteristics like fingerprints, iris scans, voice recognition, and facial recognition for authentication. Biometrics is often praised for its convenience and advanced security features, but beneath the surface lies a world of vulnerabilities that can have serious consequences.
This article will explore the growing reliance on biometrics, and the risks associated with this technology, and provide examples and statistics to demonstrate the urgent need for awareness and better safeguards.
Understanding Biometrics in Cybersecurity
Biometrics refers to the use of biological traits or behavioral characteristics to verify identity. Traditional authentication methods, such as passwords and PINs, are vulnerable to theft or brute-force attacks. In contrast, biometric data is believed to offer a more secure alternative because it is unique to every individual.
Some of the common types of biometric systems include:
- Fingerprint Scanners: Used widely in smartphones and security systems.
- Facial Recognition: Adopted for surveillance, unlocking devices, and airport security.
- Iris Scanning: Seen as one of the most accurate biometric identifiers.
- Voice Recognition: Integrated into smart assistants like Amazon Alexa or Siri.
However, while biometric technology offers convenience, it is far from perfect. The increasing integration of biometrics in critical systems raises concerns about data breaches, privacy violations, and misuse.
Growing Adoption of Biometrics
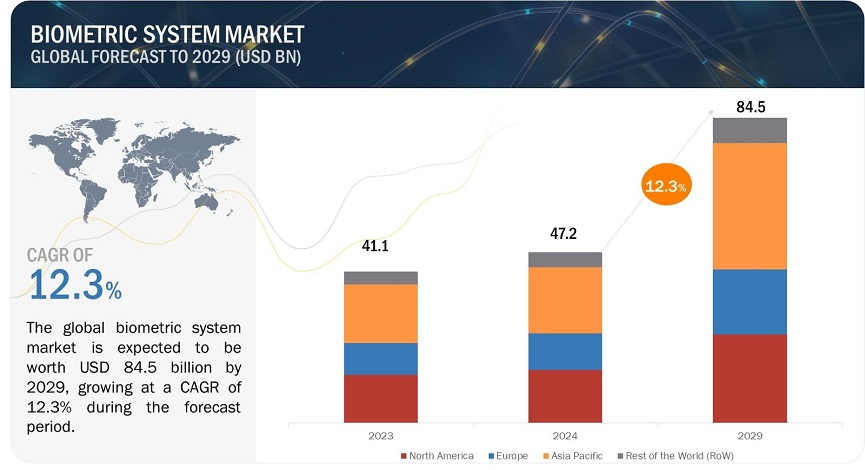
The adoption of biometric technology is increasing globally. According to a report by MarketsandMarkets, the biometrics market size is projected to reach $84.5 billion by 2029, growing at a compound annual growth rate (CAGR) of 12.3% from 2020 to 2025. Factors like the rise in security threats, digital transformation, and increased government initiatives are accelerating the shift toward biometric-based solutions.
For example:
- In 2023, 82% of smartphones globally incorporated biometric authentication.
- Facial recognition technology is widely adopted in China, where cities use it for surveillance, payment systems, and citizen tracking.
- The U.S. Transportation Security Administration (TSA) has integrated biometric checkpoints at over 25 airports across the country.
While these developments indicate technological progress, they also raise questions about privacy, security, and ethics.
The Dangers of Biometrics
Despite its appeal, biometric technology is not immune to risks. The primary concerns include:
1. Irreversible Data Breaches
Unlike passwords, biometric data cannot be changed. Once compromised, it poses permanent risks. For instance, if a fingerprint database is stolen, the affected individual cannot replace their fingerprint like they would with a password.
In 2019, the Biostar 2 data breach exposed the biometric records of over 1 million people, including facial recognition scans and fingerprint data. The breach revealed a lack of encryption and security protocols, making the data easily accessible to attackers.
2. Unauthorized Surveillance and Privacy Violations
Facial recognition technology, while useful for law enforcement and border control, can also be used for mass surveillance, raising serious ethical and privacy concerns. In China, facial recognition is reportedly used to monitor citizens’ movements and behaviors, leading to fears of government overreach and privacy erosion.
In a study by the National Institute of Standards and Technology (NIST), it was found that racial bias exists in facial recognition systems, with error rates being significantly higher for people of color compared to white individuals.
3. Deepfakes and Spoofing Attacks
Advancements in AI have led to the rise of deepfake technology, which can spoof facial recognition systems. Deepfakes involve creating highly realistic fake videos or images using machine learning. Cybercriminals can exploit this technology to bypass biometric authentication systems.
For example, in 2021, a cybersecurity firm discovered that hackers successfully bypassed facial recognition systems using printed photographs and 3D masks, highlighting the vulnerabilities in supposedly secure systems.
4. Centralized Databases Are Attractive Targets
Biometric data is often stored in centralized databases, making it a lucrative target for hackers. Unlike decentralized systems, a single breach of a centralized biometric database can expose millions of records.
For instance, in 2015, the U.S. Office of Personnel Management (OPM) suffered a massive breach that compromised 5.6 million fingerprints. The stolen biometric data potentially exposed federal employees to identity fraud and espionage.
5. Lack of Regulation and Ethical Frameworks
The rapid adoption of biometrics has outpaced regulatory frameworks, leaving gaps in protection and oversight. Governments and private organizations often implement biometric systems without proper safeguards for data privacy and security.
Real-World Examples of Biometric Risks
The dangers of biometrics are not hypothetical. Several high-profile incidents illustrate the risks:
- Indian Aadhaar Data Breach India’s Aadhaar system is the world’s largest biometric database, containing the personal information of over 1.3 billion people. In 2018, a massive breach exposed Aadhaar data, including fingerprints and iris scans, which were sold online for as little as $7. This incident raised alarms about the safety of centralized biometric databases.
- Biostar 2 Breach As mentioned earlier, the Biostar 2 breach exposed unencrypted biometric data, including fingerprints, facial recognition data, and user passwords. This breach highlighted the importance of encrypting sensitive biometric data.
- Disneyland Paris Facial Recognition Backlash In 2020, Disneyland Paris faced backlash for introducing facial recognition technology to manage visitor access. Privacy advocates argued that such systems collect excessive personal data and infringe on individual freedoms.
Amazon Rekognition Controversy Amazon’s facial recognition software, Rekognition, was criticized for its inaccuracies and ethical concerns. Tests showed that the system wrongly identified 28 U.S. Congress members as criminals, raising concerns about its reliability and racial bias.
These examples underscore the critical need for better regulation, security protocols, and public awareness around biometric systems.
Biometrics: Hero or Villain?
A comprehensive discussion on biometrics cannot ignore the question: Are biometrics the unsung hero or the ultimate villain in cybersecurity? On the one hand, biometrics offers significant advantages:
- Faster and more convenient authentication.
- Reduced dependency on passwords and PINs.
- Improved security through multi-factor authentication (e.g., combining biometrics with passwords).
However, the dangers of biometrics cannot be overlooked. Once biometric data is compromised, the consequences are irreversible. Unlike passwords, biometric identifiers cannot be reset, leaving individuals perpetually vulnerable to identity theft and fraud.
Mitigating the Risks of Biometrics
While biometric technology is here to stay, there are steps individuals, organizations, and policymakers can take to mitigate its risks:
- Adopt Decentralized Storage Storing biometric data in decentralized systems reduces the risk of large-scale breaches. Instead of centralized databases, data can be stored locally on devices, such as smartphones.
- Implement Multi-Factor Authentication (MFA) Biometric systems should be combined with other security measures, such as passwords or hardware tokens, to create a multi-layered defense.
- Encrypt Biometric Data Organizations must ensure that biometric data is encrypted both in transit and at rest to prevent unauthorized access.
- Enforce Regulatory Frameworks Governments must establish and enforce regulations to protect biometric data. The General Data Protection Regulation (GDPR) in the European Union already includes provisions for biometric data protection, but similar regulations are needed globally.
- Improve Accuracy and Bias in AI Systems Developers must address biases in facial recognition systems to ensure fairness and reduce false positives, especially for underrepresented demographics.
Conclusion
Biometrics is undoubtedly a revolutionary technology that offers convenience and improved security, but it also introduces significant risks that cannot be ignored. Data breaches, deepfake attacks, surveillance concerns, and ethical dilemmas make it a double-edged sword.
To fully harness the benefits of biometrics while mitigating its dangers, organizations must prioritize encryption, decentralization, and ethical frameworks. Governments, too, must step up with stringent regulations to protect citizens’ biometric data from misuse. Ultimately, the future of biometrics will depend on how well we can balance innovation with security and privacy.
As biometric systems continue to evolve, individuals and organizations alike must remain vigilant. Cybersecurity in the biometric age is not just about protecting systems but safeguarding our identities and freedoms.