The Quickfox VPN is mainly used by Chinese citizens living abroad who need to access Chinese websites as most of these sites are geo-restricted.
Wizcase’s team of ethical researchers, led by Ata Hakcil, discovered a “critical leak” that the researchers found to be exposing personally identifiable information of at least one million users of a Chinese VPN service.
The team revealed that the VPN leaking data is Quickfox, produced by Fuzhou Zixun Network Technology Co., Ltd.
The VPN is mainly used by Chinese citizens living abroad who need to access Chinese websites as most of these sites are geo-restricted. The VPN connects to servers in China and lets users avoid those restrictions.
What Happened?
Reportedly, the leak was caused by a misconfiguration in the VPN. The product had insufficient ELK (Elasticsearch, Logstash, and Kibana) stack security, which refers to the three open-source programs responsible for streamlining searchers via large files, in this case, the logs of Quickfox.
SEE: Almost Every Major Free VPN Service is a Glorified Data Farm
Researchers identified that Quickfox had set up access restrictions from Kibana but hadn’t set up security measures for the Elasticsearch server. Hence, anyone with an internet connection and a browser could access Quickfox and retrieve sensitive PII information on the service’s users.
What’s worse is that there wasn’t any password protection in place or login credentials required to access the data, but the data wasn’t encrypted.
What Information was Leaked?
The 100GB database contained around 500 million records, including PII of nearly one million Quickfox users. PII data included:
- Names
- Device data
- Device type
- phone numbers
- email addresses
- MD5 hashed passwords
- Software installed on the device and installation date.
The data is enough for scammers to launch phishing attacks, vishing phone calls, and other schemes to obtain banking data. The server was yet not secured until the time of this writing.
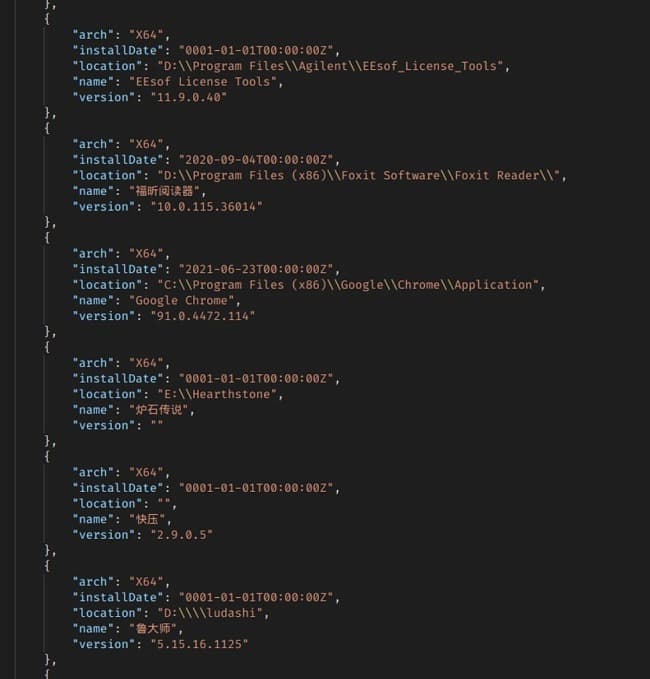
Screenshot shared by WizCase shows a List of installed software on a random users device by name, install date, and version
“All the documents found were dated between June 2021 and September 2021,” Wizcase researchers wrote in their report. “The leaked information about device type and installed software could make this con very convincing. It’s unclear why the VPN was collecting this data, as it is unnecessary for its process and it is not standard practice seen with other VPN services.”
SEE: 7 VPN with no-logs policy exposing 1.2 TB of user data
Impacted users were mainly located in the following countries:
- USA
- China
- Japan
- Indonesia
- Kazakhstan
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.
Credit: Source link




















