Information security standards such as PCI DSS and ISO 27001 and regulations such as HIPAA and CMMC mandate system hardening as one of the most basic defenses against cyber intrusions.
The reason for this should be obvious to anyone: What’s the point of implementing more advanced security measures and protections if you don’t first bolt all the unnecessary “doors” through which attackers can enter your systems and networks?
What is system hardening and what are the associated challenges?
System hardening is the process of configuring IT infrastructure – servers, databases, networks, operating systems, and applications – to minimize the organization’s attack surface, i.e., the vectors and vulnerabilities cyber attackers may exploit to gain access to and control over it.
Increased security is one of its goals, but there are others: regulatory compliance, long-term cost savings, and enhanced operational stability.
What does system hardening encompass? Let’s take server hardening as an example. According to the NIST SP 800-123 Guide to General Server Security, server hardening should include:
- Configuring the underlying OS and user authentication (e.g., disabling unneeded default accounts, creating only necessary accounts, create specific user groups with specific rights, etc.)
- Removing or disabling unnecessary services, applications, and network protocols (e.g., file and printer sharing services, system and network management tools, ports, etc.)
- Configuring appropriate access controls to resources (limit read and write access, limit execution of system-related tools to sysadmins, etc.).
Sounds simple, no? But what if you must do it all for several hundred or thousand different servers? And, most importantly, can you prevent these configurations and modifications from being inappropriately altered as time passes?
Roy Ludmir, business development manager at Isreali company CalCom, says that there are two categories of tools that can be used for server hardening (though that’s not their main purpose): compliance scanners and configuration management tools.
But while the former focus on pointing out configuration drift from specific compliance frameworks, and the latter can do that as well as enforcing hardening policies/configuration changes, they don’t provide a solution for the entire hardening process like their CalCom Hardening Suite does.
“None of them replace the need for lab testing to simulate the impact of security policies on servers before they are enforced, and none of them help reduce the complexity of change management and enforcement of multiple policies on a complex infrastructure,” he says.
In addition to that, the suite allows IT operations and IT security teams to make server hardening a continuous process rather than a one-time task, as well as to maintain their organization’s compliance posture over time, despite updated policies and changes introduced in the infrastructure.
Server hardening minimizes the risk of infrastructure downtime
Organizations that juggle more than a couple of hundred of servers with a multitude of configuration options and must deal with a constantly changing infrastructure can’t hope to manually perform constant and thorough server hardening.
Just think about it:
- A hardening project must start with an analysis of the impact hardening policies will have on the production infrastructure before any configuration changes are made (Never test hardening on production servers!)
- Different hardening policies must be implemented for different systems (and mistakes avoided or easily rolled back)
- Constant policy and infrastructure updates might affect the compliance posture, meaning compliance-focused scanning should be near-constant.
Of these, the step that’s most difficult to perform quickly and accurately is the impact analysis.
To see how your hardening policies will affect your production environment, you need to build a test environment that will accurately reflect its complexity, as well as simulate the traffic, the number of users in the network, and various dependencies. This is a grueling task to perform manually, and there’s a high chance of error that could lead to costly production downtime.
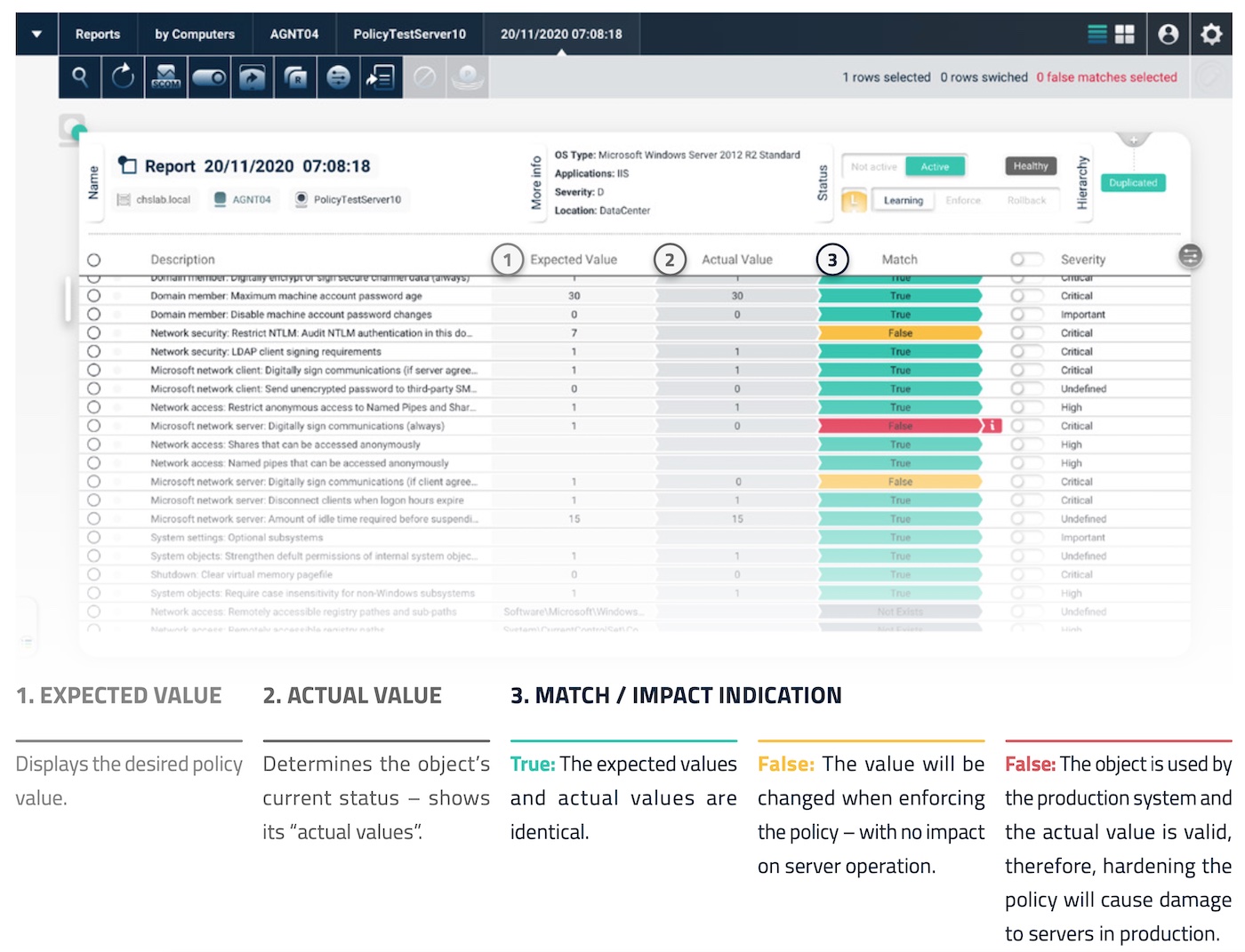
CalCom Hardening Suite minimizes this risk thanks to its automated processes. After its software agents are installed on the servers, it starts the so-called learning mode, during which it collects data from different sources on the machines and analyzes it to understand how the proposed policies will impact system operations.
The resulting report lists each proposed policy, its desired value, and its current value. If these values match, it means that no changes will happen when the policy is enforced. If they don’t, the solution differentiates between values that will be changed when enforcing the policy with no impact on server operation, and values that, if changed, will lead to production server disruption.
Based on this analysis, the solution creates the optimal policy implementation plan for each server that will maximize policy compliance while avoiding impact to production.
The next step – policy enforcement/implementation – is often performed by organizations via configuration management tools and Group Policy Objects (GPOs). If the policies are maximally granular – as they should be to suitably harden the different environments, machine types and roles – this can also be a time-consuming nightmare for IT operations teams that don’t have an automated solution at their disposal.
CHS, on the other hand, can push configuration changes on the entire production server fleet from a single point of control. This enables organizations to assign the privileges needed to change system configurations only to a minimal number of users, thus minimizing human error.
Finally, CHS prevents configuration changes that are against the enforced policies – no matter whether they are performed by malicious actors or are the result of a simple error. It also notifies the security team about the attempt to change the configuration by sending alerts to a SIEM or SOC solutions in use.
Conclusion
CalCom Hardening Suite is available for servers, middleware applications and endpoints.
Keren Pollack, CalCom’s marketing manager, says that their clients are mostly insurance companies, financial institutions, healthcare companies, and DoD contractors – companies that must comply with regulation that requires system hardening. Companies that support critical infrastructure are also prospective clients.
Customers can use the solution with minimal support from CalCom, but the company also offers additional guidance and advice to customers, if needed.
“We have the in-house knowledge to help organizations build effective system hardening policies. They are usually based on our own hardening recommendations, special organizational needs, and industry best practices and benchmarks (e.g., CIS, NIST, DISA STIGs, and so on),” Pollack explained.
“After the initial policies are defined, the organization needs to have another policy discussion after CHS’s learning process is done, to decide what they are going to do about each hardening action they can’t implement without adversely affecting production. We can be involved in this process and help them choose the right course of action.”
Credit: Source link