Linux and macOS samples of SysJoker malware were found to be fully undetected on VirusTotal.
The IT security researchers at Israel-based cybersecurity firm Intezer have identified a novel multi-platform backdoor malware that’s targeting all mainstream operating systems, including Windows, macOS, and Linux.
Researchers believe it could be the work of an advanced threat actor. Intezer claims that the first evidence of this malware, dubbed SysJoker, was discovered in December 2021 in an attack against a Linux-based web server of an unidentified, well-known educational institution.
SysJoker Technical Analysis
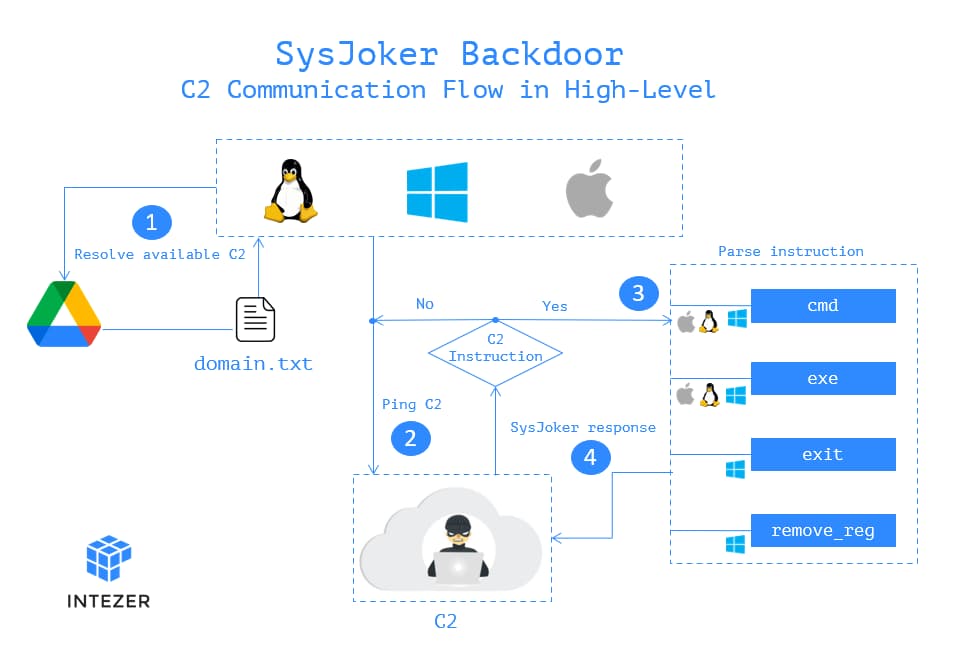
In their report, Intezer researchers Ryan Robinson, Avigayil Mechtinger, and Nicole Fishbein wrote that SysJoker disguises itself as a system update and establishes its C2 server by decoding “a string retrieved from a text file hosted on Google Drive.” It might be having some specific targets.
Related: CrossRAT keylogging malware targets Linux, macOS & Windows PCs
Based on victimology and malware’s behavior, researchers assess that SysJoker is after specific targets. Further probe revealed that the attacks involving SysJoker started in mid-2021.
The malware is written in C++, and each sample is designed to target a specific operating system. The backdoor establishes initial access on the targeted device, and after getting installed, it executes follow-on code and new commands so that attackers can launch follow-on attacks. They can also penetrate deeply into a corporate network at this stage.
Attack Vector
Researchers revealed that the probable attack vector for SysJoker backdoor malware is a compromised npm package, a pretty common vector used to drop malware on targeted machines. Public code repositories like NPM are centralized developer communities where coders can upload/download building blocks when developing applications. If any of these building blocks is malicious, it might get into several apps and strike unsuspecting users.
Malware Capabilities
After SysJoker is executed, it lays low for some time, such as a minute or two, and then creates the C:ProgramDataSystemData directory where it copies itself using “igfxCUIService.exe” filename.
This means it hides as the Intel Graphics Common User Interface Service. It then collects key system data such as username, mac address, physical media serial number and IP address and dumps the data into a temporary text file. This file is immediately stored in a JSON object and deleted. It is then encoded and “written to a file named ‘microsoft_Windows.dll,” researchers wrote.
Related: Old crypto malware makes come back, hits Windows, Linux devices
The malware establishes persistence by adding an entry to the registry run key identified as “HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun.” It is worth noting that SysJoker sleeps for a random period between each stage of infection.
It is concerning that Linux, and macOS samples were found to be fully undetected on the malware scanning platform VirusTotal.
“Based on the malware’s capabilities, we assess that the goal of the attack is espionage together with lateral movement which might also lead to a Ransomware attack as one of the next stages,” Intezer researchers concluded in their report.
Did you enjoy reading this article? How about following us on Twitter @HackRead and Like us on Facebook @ /HackRead?
Credit: Source link