Automotive, medical device and industrial equipment manufacturers are building critical devices we all rely on – from the cars we use to commute, the equipment that keeps the lights on at night, to the heart valves that save human lives.
But with software being developed and integrated with open-source code, and endless supply chain components upon which we have limited control, we are encountering security risk levels never before encountered. Throughout the life of the product, from design to development and into post production, the security risk posture changes countless times, with every software component added, open source threat discovered or CVE exposed.
The product security practices we rely on are simply not built for today’s devices, and for the most part, they are static and limited. They are either too limited or applied way too late in the product life cycle, often leading to costly recalls, device re-architecture, and a direct hit on the organization’s brand and reputation.
Product Security Lifecycle Platform
Cybellum’s Product Security Lifecycle Platform enables device manufacturers to secure their products throughout their entire life – from first design to operational use, and years after.
Powered by Cyber Digital Twins technology – a live, highly detailed digital replica of every software component inside the device – Cybellum continuously and automatically scans the device system for risks, with every firmware change or vulnerability discovered. Product security teams can manage, mitigate and report on their security posture on an ongoing basis, across all supply chain tiers and product lines.
Leading automotive, medical device and industrial equipment manufacturers use Cybellum to ensure that their new, in-development and legacy devices are regulatory compliant and secure.
The Cybellum platform provides the infrastructure and means needed to develop and maintain secure products at scale, with Cybellum Product Security Assessment and Product Security Operations.
Product Security Assessment
Cybellum Product Security Assessment enables automatic exposure of cyber risk in binary code throughout the product design and development phase and in mission-critical microcontroller based components. No source-code is needed.
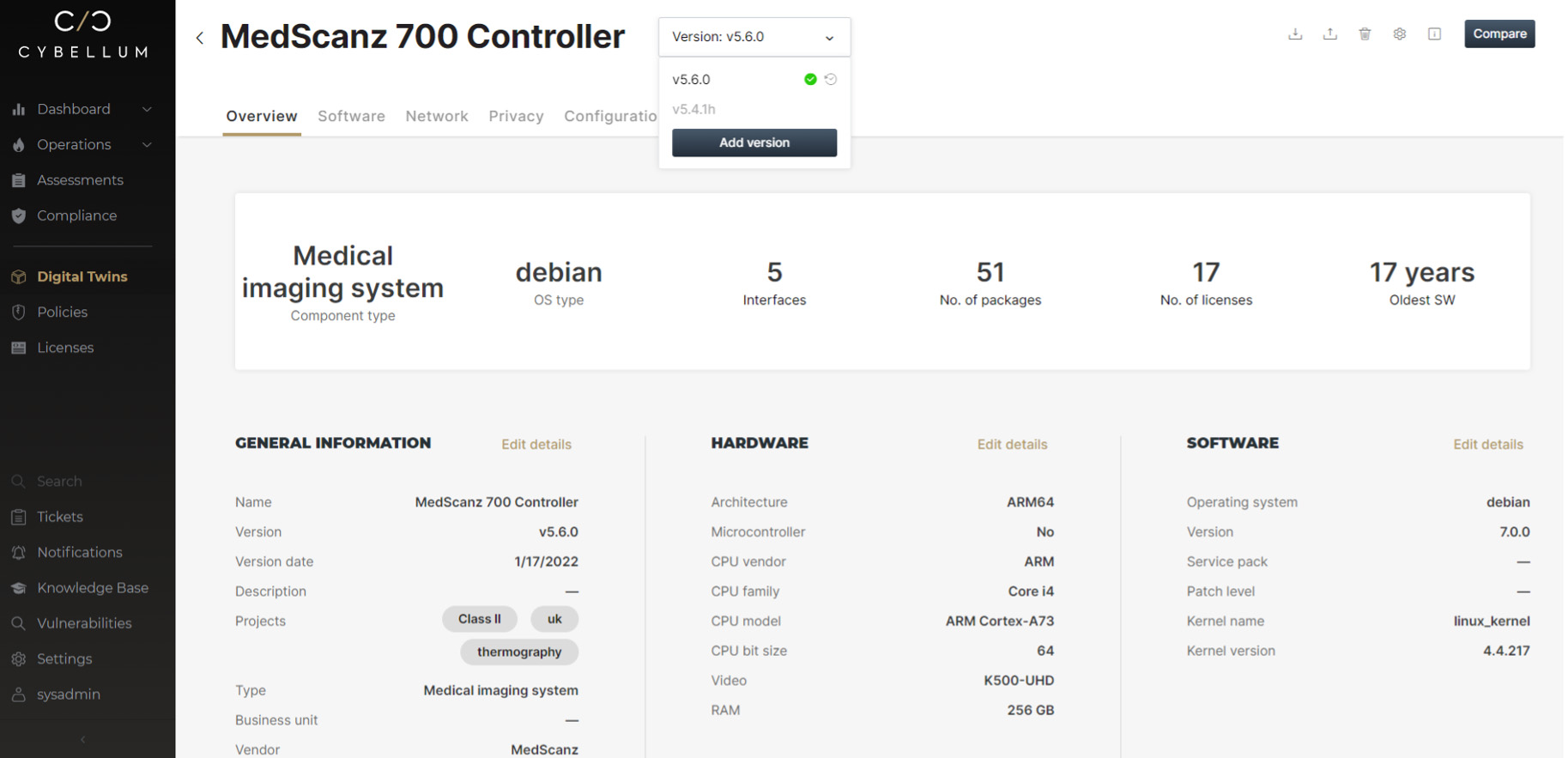
It reveals all product characteristics (hardware architecture, operating systems, SBOM, licenses, configurations, control flow, APIs and more), enabling SBOM management and supply-chain oversight, automated vulnerability management and compliance with regulations and policies.
Product Security Assessment analyzes proprietary code (i.e. not open-source software), exposing zero-day weaknesses that may introduce significant cyber risks, such as remote code execution or DoS attacks. It validates compliance with software licensing and security policies, including industry regulations and standards, secure coding best practices (e.g. CERT C/MISRA), cryptography related issues (e.g. use of weak hash-functions, private PKI keys in the code), privacy violations and more.
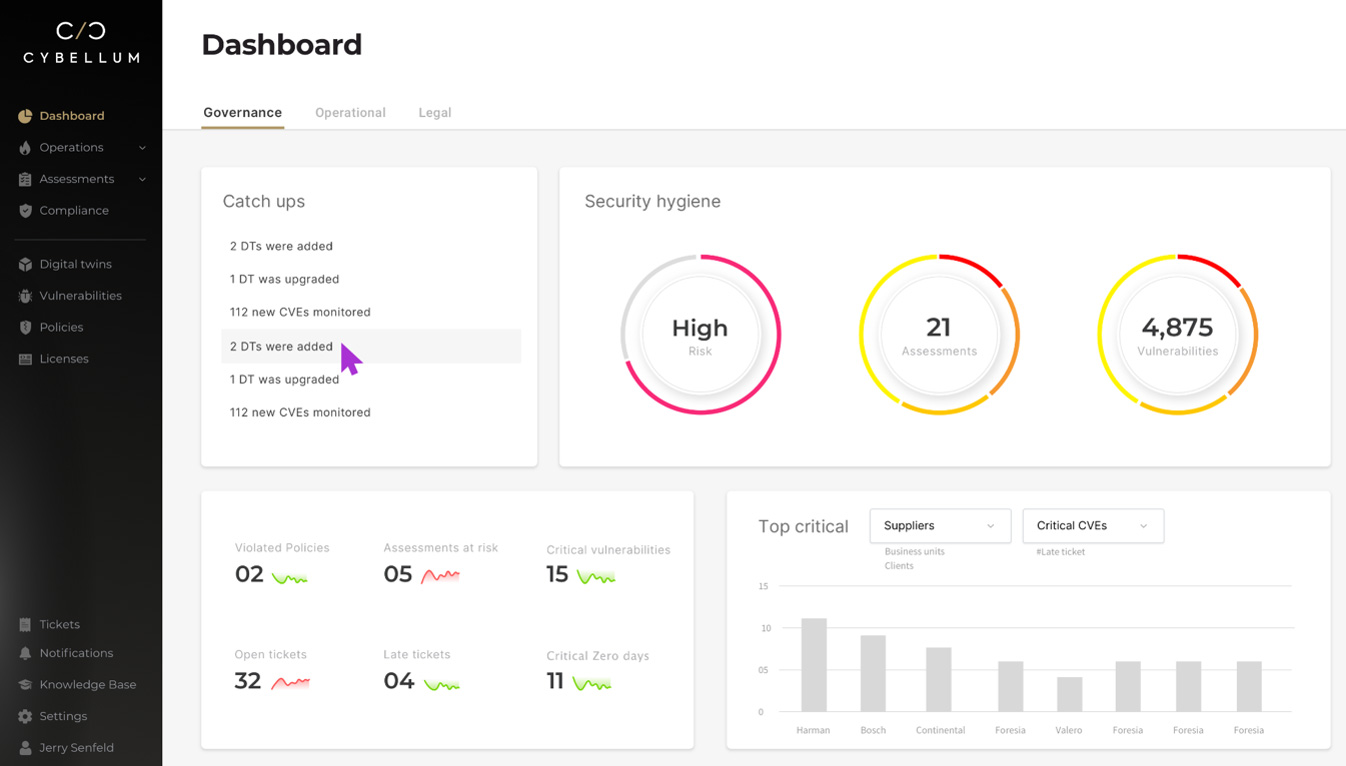
It includes governance dashboards for managerial oversight over security, licensing and compliance operations, enabling continuous reduction of risk and improvement of the organization’s security posture.
Deployed on-prem or in the cloud, Product Security Assessment is an agentless solution that integrates seamlessly with your ALM/PLM, CI/CD systems, asset-management, ticketing solutions, and more.
Product Security Operations
Cybellum Product Security Operations continuously monitors all components and product post-production, for new vulnerabilities and threats across public, private and dark-web sources, and tracks changes in severity of previously known vulnerabilities. It automates threat intelligence gathering and impacts assessments, facilitating prioritization of security issues, based on the real risk they pose to your devices.
By providing mitigation recommendations and integrating with remote software update systems, Product Security Operations cuts down incident response times, keeping products and users safe and secure. Deployed on-prem or in the cloud, it is an agentless solution that integrates seamlessly with existing SDLC, asset-management, SOC and PSIRT systems.
Supported uses cases cyber BOM management
With complete visibility and validation of the underlying device software components, Cybellum facilitates supply chain oversight, and security and compliance validation during development, and quick impact assessment and incident response post production.
Automated vulnerability management
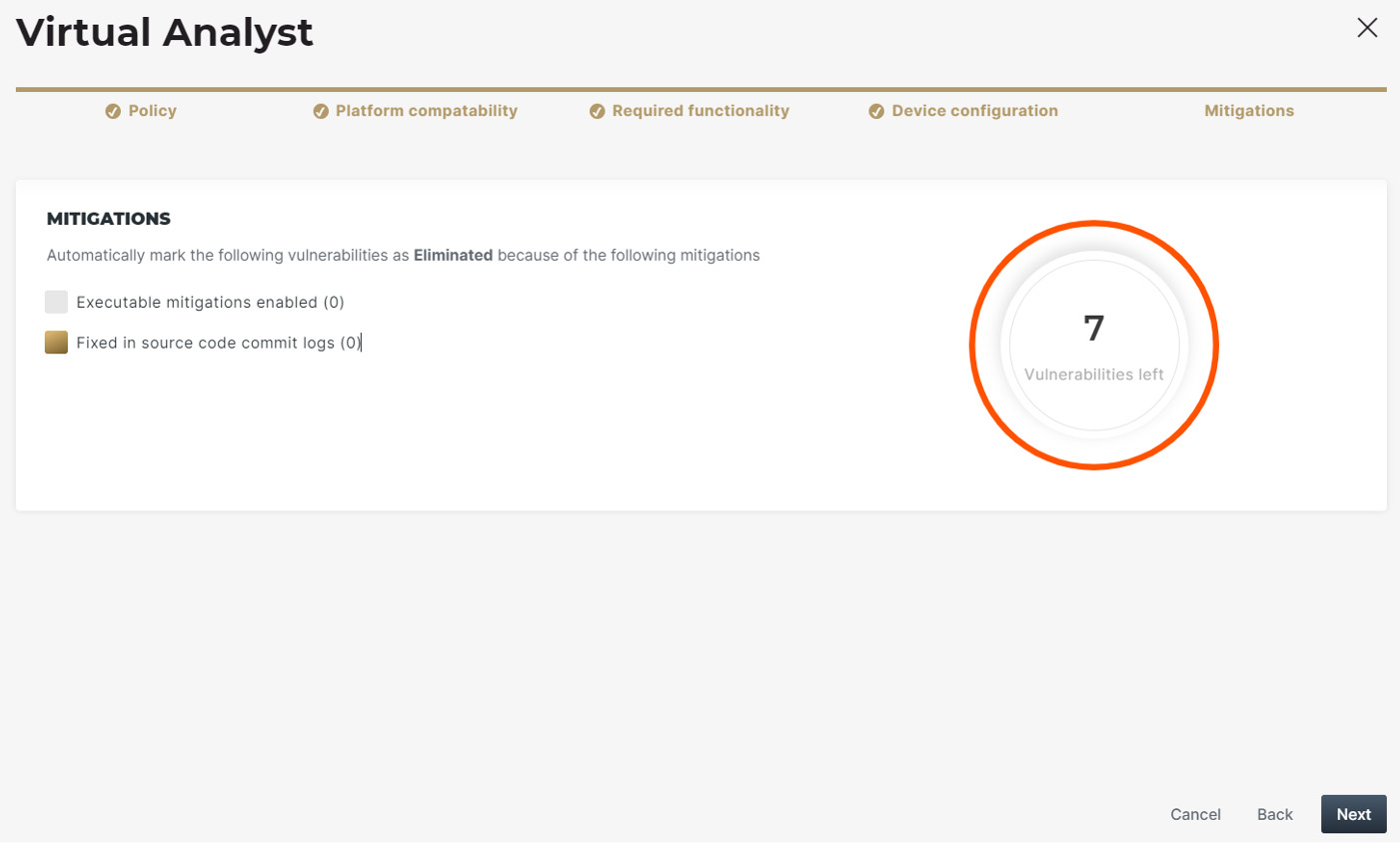
Continuous vulnerability management, assisted by the “Virtual Analyst,” enables product security teams to scale their operations in light of growing software complexity and expanding attack surfaces.
Red team automation
Automated exposure of zero-day coding weaknesses with insights into possible exploitations, reduces the amount of manual work required by Red Teams, empowering them to quickly and efficiently expose security issues.
License policy enforcement
Built-in licensing policies with extensive customization capabilities enable automated, frictionless enforcement of company licensing policies, reducing the legal risk associated with the use of open-source software packages.
Threat hunting
Continuous monitoring of aggregated threat intelligence from multiple public / private resources, coupled with automated impact analysis, enables quick and efficient incident response by SOCs and PSIRTs.
Governance and compliance
Proactively manage product security by tracking relevant metrics (critical vulnerabilities, open tickets with internal teams/external suppliers, risk trends etc.) to facilitate compliance, including report generation for auditing/compliance processes.
Ready to see the platform in action? Book a demo with one of our experts.
Credit: Source link