Delivering secure applications requires tooling built for automation in the modern tech stack. Oxeye provides a cloud-native application security testing solution that is designed to overcome the challenges imposed by the complex nature of modern architectures. Given the distributed cloud-native architecture, traditional testing methodologies simply aren’t enough to address security holistically.
Oxeye disrupts traditional application security testing (AST), approaches by offering a contextual, effortless, and comprehensive solution to ensure no vulnerable code ever reaches production. Traditional AST approaches rely on heavyweight, one-time gating inspections, typically performed late in testing, and requiring security professionals to perform them. With modern cloud-native applications, security needs to start at the very beginning of the application creation and throughout the DevOps and Development processes, it must be continuous, automated, and improved with each subsequent iteration in the application development life-cycle.
Cloud-native application security testing
Oxeye is designed to analyze your applications, external libraries, and 3rd party packages. Our solution helps to identify and remediate OWASP TOP 10/API TOP 10 code vulnerabilities of cloud-native apps.
Our disruptive technology analyzes code vulnerabilities across microservices delivering contextualized risk assessment enriched with infrastructure configuration data.
Oxeye tests your applications during the CI/CD process without adding any line of code. We identify code vulnerabilities and highlight the most critical ones as an integral part of your software development lifecycle, and deliver clear guidance for remediation. Getting started with Oxeye is very simple, it only requires integrating one component into your cluster without changing any line of code.
Eliminate Noise. Unleash DevOps. Scale AppSec.
Oxeye is designed to expose vulnerable flows in distributed cloud-native applications code. We incorporate next-generation SAST, DAST, IAST, and SCA capabilities to ensure verification of risks in both Dev and Runtime environments. Built for developers and AppSec teams, Oxeye helps to shift-left security while accelerating development cycles, reducing friction, and eliminating vulnerabilities.
Multi-layer multi-service analysis
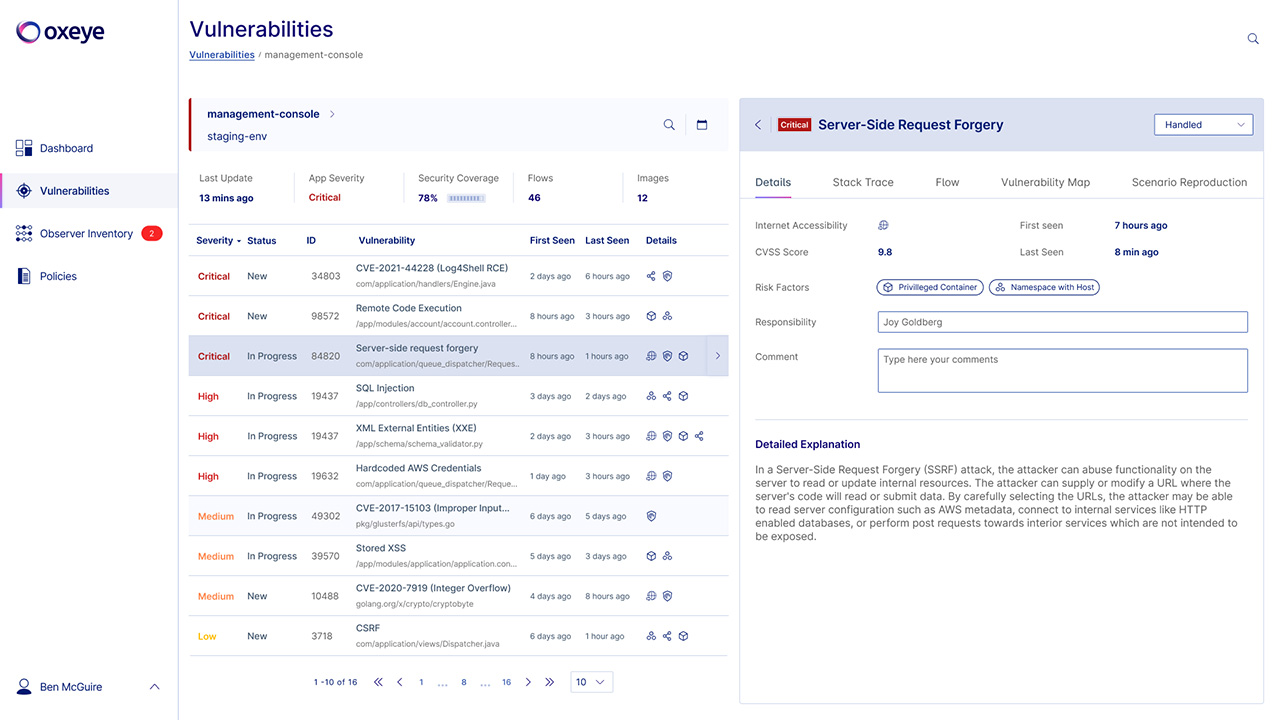
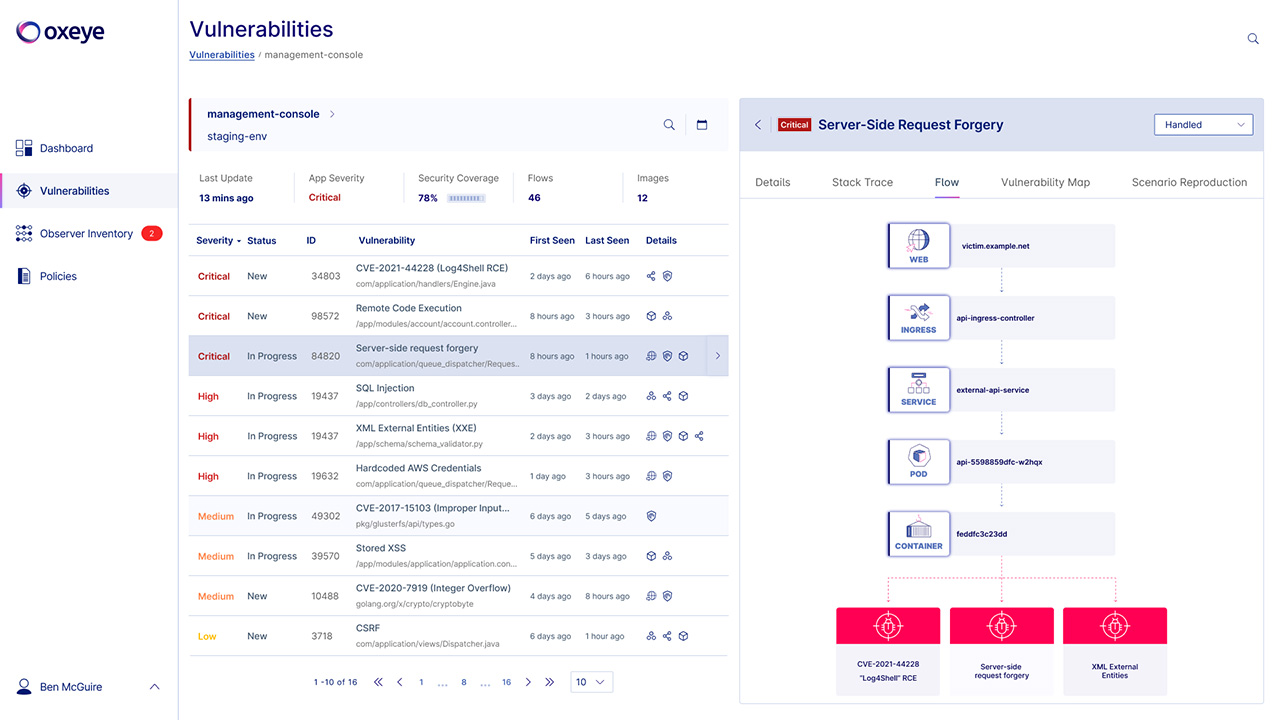
With cloud-native applications, pieces of code are deployed in several places, communicate in runtime and run on different parts of the infrastructure. Oxeye performs automated risks analysis enriched with your environment data – cloud, clusters, and containers to deliver full contextual vulnerability flow.
Oxeye helps Developer and AppSec teams to understand the context of vulnerabilities, saving them time and effort by providing clear remediation guidance and reproduction scenarios.
Seamless integration, agentless approach
With a single deployment as Daemonset into your cluster, and without the need to perform changes in the code, Oxeye delivers a fully automated solution for cloud-native application security testing. Given the complexities of cloud-native architecture, traditional testing methodologies simply aren’t enough to address security holistically.
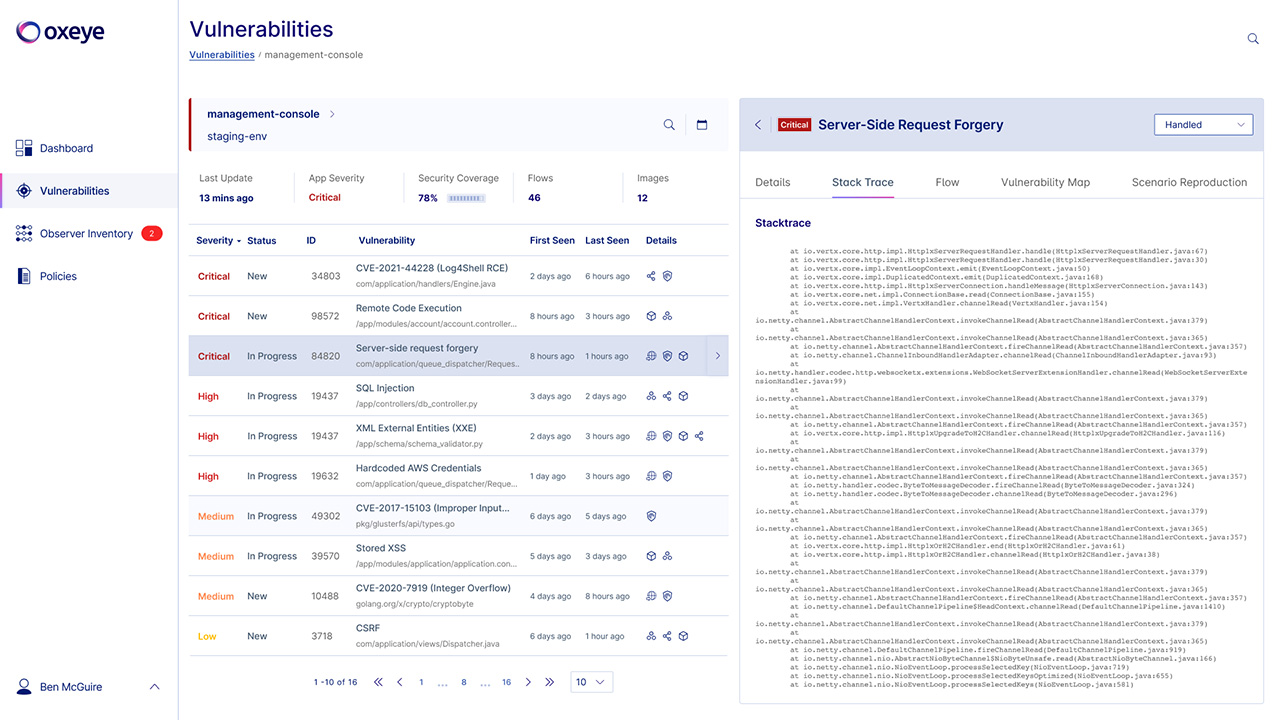
Oxeye helps to empower developers to handle security vulnerabilities early on, prior to production. Developers can easily track and resolve vulnerabilities leveraging Oxeye’s visibility flow, steps to reproduce, and the exact line of code that the vulnerability resides.
Reliable results with high accuracy
Accuracy has long been the issue of legacy application security testing (AST) solutions. In order to automate security for cloud native apps, the results must be reliable, accurate, and with context. While most AST tools are strictly focused on finding vulnerabilities, Oxeye provides rich vulnerability context while limiting the noise of false positives/negatives.
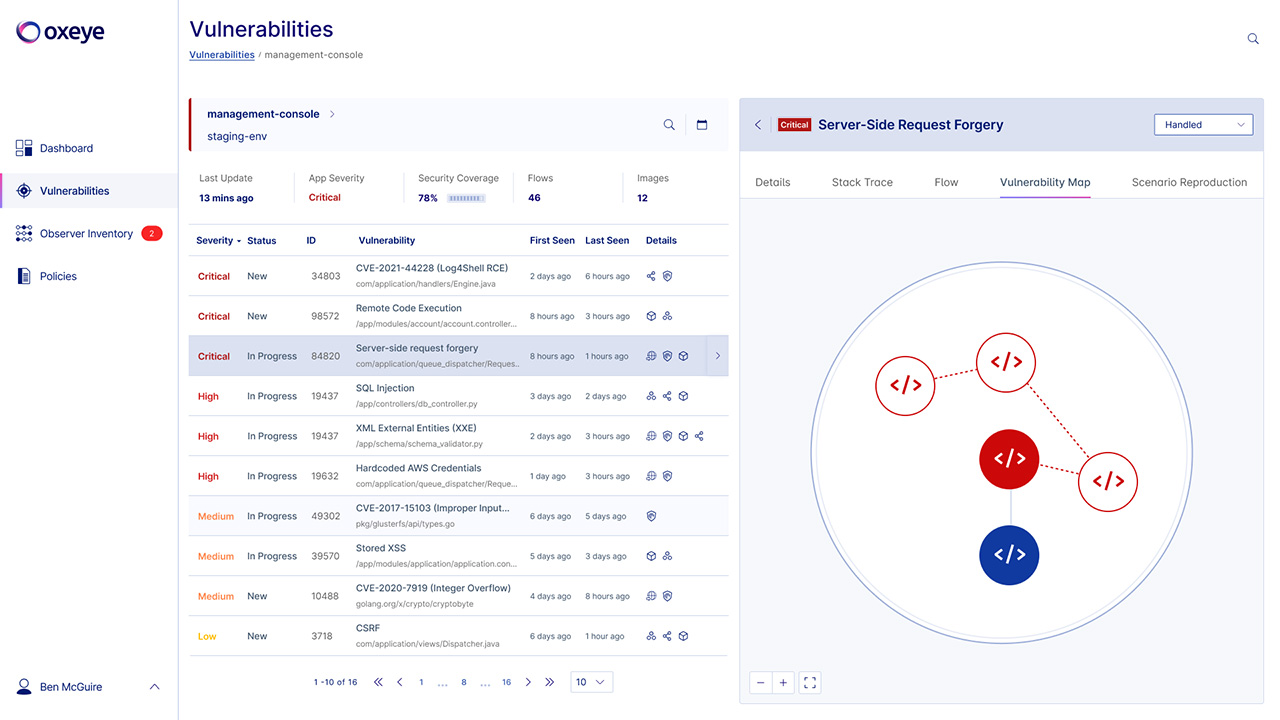
Oxeye helps you uncover critical vulnerabilities earlier in your CI/CD pipeline. Teams automatically get maps of application logic and inner communications between code components for comprehensive analysis and visibility. Harness our powerful solution and leverage the rich vulnerability context we provide from each phase of the application flow to better understand the risks you are facing.
Credit: Source link