In July 2021 the REvil ransomware group vanished due to mounting US pressure after the Kaseya attack. However, the group was back in September 2021 by carrying out extortion-based DDoS attacks on ITSPs in the UK and Canada/America.
The infamous REvil ransomware group has suddenly announced to end its activities. The group, which gained prominence over cyberspace with high-profile ransomware attacks against Kaseya, JBS, and Travelex this year, has reportedly decided to go underground after its Tor payment portal and data leak blog were hijacked.
The news of REvil’s shutdown was posted on a well-known criminal forum run by a threat actor “0_neday” suspected to be associated with the gang and was first reported by Dmitry Smilyanets from Recorded Future.
It is worth noting that in July 2021, the REvil ransomware group vanished due to mounting US pressure after the Kaseya attack. However, the group was back in September 2021 by carrying out extortion-based DDoS attacks on ITSPs in the UK and Canada/America.
REvil Announces Shutdown
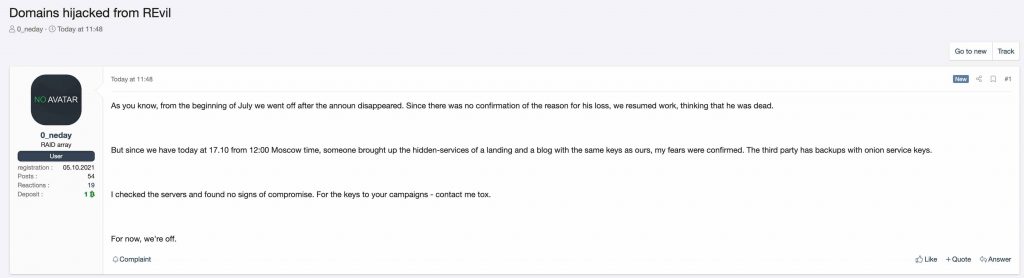
The post where the group announced the closure of its activities revealed that the REvil gang’s Tor services were allegedly hijacked and whoever hacked it replaced the services with a copy of the gang’s private keys, which they must have obtained from a previous backup. The server was claimed to be “compromised,” and the group stated in the post that “they were looking for me.”
“To be precise, they deleted the path to my hidden service in the torrc file [used for configuring the Tor service] and raised their own so that I would go there. I checked on others — this was not. Good luck everyone, I’m off,” REvil operator(s) noted in the post.
As shown in the screenshot below, the operator used the infamous Russian language hacker forum XSS.IS to publish their post:
Who Hijacked REvil’s Tor Sites?
At the moment, there’s no clarity regarding who could have hijacked REVil’s Tor sites. According to The Washington Post, the FBI had managed to access encryption keys used by the REvil gang for the Kaseya attack in July. But the agency couldn’t take down the gang.
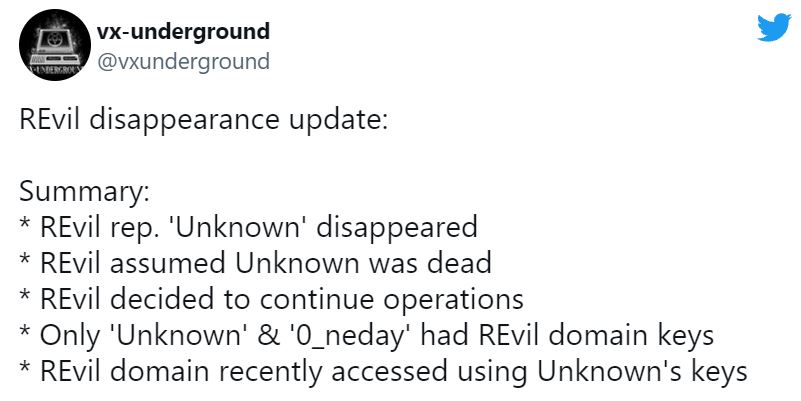
There are rumors that the Tor sites have been taken over by a former member of the REvil group known as Unkn/Uknown, who has been a spokesperson for the gang but didn’t accompany them when the group resurfaced in September 2021.
A website called VX-Underground tweeted that just Uknown and the threat actor on whose forum REvil’s closure statement was posted had access to domain keys, and the ransomware gang’s domain was accessed recently with Unknown’s keys.
“Since there was no confirmation of the reason for his loss, we resumed work, thinking that he was dead. But since we have today at 17.10 from 12:00 Moscow time, someone brought up the hidden-services of a landing and a bog with the same key as ours, my fears were concerned,” the threat actor explained.
However, in a conversation with Hackread.com, Steve Moore, chief security strategist, Exabeam said that, “This latest disruption seems to be caused by insider fighting or possible offensive takedown – it’s the final blow to REvil. The operator only mentions a “third party” – no attempt is made to identify their identity.
“Keep in mind these are organizations like any other, but with fewer rules. Based on information shared, they lost control of their backups which contained keys to overtake their network. In the exciting twist, the adversary was seemingly taken down due to weak technology hygiene, a flaw generally exploited by them to extort money from their victims, ” Moore added.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.
Credit: Source link