In a 2019 spoofing attack, malicious actors rerouted user clicks and generated Bitcoin using supposedly legitimate BBC News webpages. Spoofing attacks like this are quite common in today’s cyber landscape. When you consider that a staggering 3.1 billion domain spoofing emails are sent daily, according to a report by Proofpoint, you realize just how critical spoofing is to the attack cycle. With increased digitization across enterprises in 2022, especially on the back of the COVID-19 pandemic, malicious actors now have a larger attack surface to exploit.
In fact, cybersecurity projections from the World Economic Forum showed that supply chain attacks like the SolarWinds hack would increase this year — and they did (you can find the 5 biggest supply chain attacks in 2022 so far here, according to security blog ImmuniWeb). The pace isn’t going to slow down next year, as experts note we will see more of such attacks in 2023. Considering the level of havoc that a hack can wreak, like irreparable damage to brand reputation and serious financial losses, every organization must now prioritize adopting a proactive, rather than reactive, approach towards cybersecurity in the coming year.
While spoofing may seem like a simple hacking technique, a number of notable, high-profile organizations have suffered severe financial and reputational damage from spoofing attacks. Bad actors are getting more sophisticated by the minute, with a survey from McKinsey stating that companies’ cybersecurity measures aren’t keeping pace with today’s business environment demands. Learning how to win the spoofing war against cyberattackers in 2023 could be the difference between protecting your business and scrambling to pick up the pieces in the wake of an attack later down the road
Don’t choose the reactionary side of the cybersecurity equation next year. Yes, spoofing attacks will grow even stronger, but organizations that prepare ahead will enjoy peace of mind and rest easy, even in the midst of the impending cyber chaos.
Here’s how you can win the spoofing war in 2023.
Spoofing basics
First, let’s understand what spoofing means. Spoofing is really a game of deception. The word “spoof” literally means “fake”. Someone somewhere acting like someone somewhere else to steal something valuable— that’s spoofing.
For a more technical definition, Gartner defines spoofing as “a process whereby a router responds to keep-alive messages from a host rather than passing them on to the remote client, thus saving call charges— used mainly in Integrated Services Digital Network (ISDN).” In other words, a would-be cybercriminal pretends to be someone or an organization that you trust to gain access to your personal information.
It often starts the cycle of larger attacks like advanced persistent threats (APT) and man-in-the-middle (MITM) attacks, aiding threat actors in their mission to take charge of your critical assets.
What you should watch out for
There are several ways cybercriminals can use spoofing to break through your network security and get ahold of your sensitive data, client lists, internal communications, trade secrets, or whatever crown jewels of data are important to your organization. Spoofing can look like any of the following:
1. Minor typo errors
An email with a minor error like using an “I” in place of an “L” is more than a typo— it could be a sign of something seriously suspicious. Some hackers use Cyrillic characters that are similar to Latin script to create fake website URLs that, at first glance, may look exactly like the real thing. For example, “www.whatsapp.com” might be written as “www.шhatsapp.com”. Notice that the “w” in the second URL contains the Cyrillic letter “ш”.
If a website seems just a little bit off, then there’s a high chance that something is wrong with it. Your security mantra should be: “If it seems off, then it’s probably off.”
2. Incorrect domain names
Sometimes, hackers buy out domains that are common typos for major websites and companies, in the hopes that one slip of your finger could land you in their trap. These sketchy sites often use the same fonts and color schemes as their legitimate counterparts. From there, you could end up entering your data into a nefarious site, all while you believe that you’re accessing a legitimate site. A great example is an incorrect domain name like facebook.business.com instead of the correct business.facebook.com.
3. Generic email domains for large companies
National banks aren’t going to be contacting you from @gmail.com or @yahoo.com email address. If you get a message from a supposed “government official” or “bank official” using such emails to ask for your personally identifiable information (PII) like your credit card details or passport number, then you’re most likely getting spoofed.
4. Forced urgency
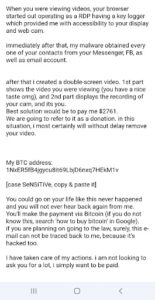
The screenshot above shows an email I received from one Todd Green on November 19, 2021, who claimed he had hacked one of my emails to get my password. True, he had gotten a password of mine, but it was an old password that I used about 10 years ago and had since changed. His intention was to pressure me into making a swift but silly decision.
Just like what happened to me, hackers will often try to pressure you to do things immediately, forcing you to make immediate but irrational decisions. Are they asking you to send things over right away? Telling you your bank account will close if you don’t update your password by entering your old one? Then that’s something to suspect.
Winning the war against spoofing attacks in 2023
At this stage, spoofing is more advanced than ever before and organizations must implement a strong zero-trust approach in all aspects of their cybersecurity strategies going into 2023, or risk potentially disastrous consequences. The zero-trust approach is rooted in the principle of “never trust, always verify,” according to Palo Alto Networks. IT teams and employees across the board must adopt a verification-before-authentication culture to mitigate the possibility of a hack.
To win the spoofing war in 2023, here are some vital steps you should take:
- Check domain names for typos or any strange-looking alphabets. If you find any such alphabet, beware.
- Keep an eye out for incorrect grammar, poor spelling, and any funny-looking sentence structure, syntax, or wording.
- Run a search on Google to see if strange-looking emails or websites show up. Also, copy and paste any email texts you consider to be spoofed. You’ll most likely find such texts have been reported and published online.
- Don’t click unfamiliar links or download attachments from untrusted sources.
- Confirm the legitimacy of any unfamiliar links. When was the website registered? If it’s new, it’s likely not legitimate.
- Never share your password with anyone. Your bank already has your password on file, so they won’t ask you for it— even to confirm it’s you.
- Ensure you never use unprotected privacy settings. Be security-conscious at all times.
- Organizations must conduct regular cybersecurity awareness training for all their employees to keep them abreast of the latest cybersecurity developments, including trending attacks.
Vigilance is the key
Vigilance is the key to staying one step ahead of spoofing attacks. Since spoofing is a game of deception, constant vigilance is essential. As it is with all games of subtlety, people who stay inattentive often become victims. So, be on the lookout for anything that seems a little bit “off”.
Remember; “if it seems off, then it’s probably off.” If you aren’t sure, play it safe! You can always google the site. Go to the domain on Google, or call support to confirm the email is legitimate.
Stay alert. Never trust. Always verify. That’s how to win the war.