In the intricate world of cryptocurrency, newcomers frequently grapple with fundamental questions about the security of their digital assets. One persistent and particularly intriguing query revolves around the possibility of generating cryptocurrency wallets by systematically exploring mnemonic phrase combinations using modern computational power.
At the heart of this curiosity lies what’s known in the crypto community as the “mnemonic phrase collision generator” – a concept that sounds tantalizing but crumbles under mathematical scrutiny. Let’s dive deep into the numbers that definitively debunk this potential security threat.
The BIP39 Standard: Calculating Combinatorial Complexity
The BIP39 standard utilizes a comprehensive word list containing 2,048 unique words. When we calculate the possible combinations for a 12-word mnemonic phrase, the numbers become mind-bogglingly large:
Precise Calculation: P(2048,12) = 2048!/(2048-12)! ≈ 5.27 × 10^39 total possible combinations
To contextualize this astronomical number, let’s consider the computational power of a state-of-the-art NVIDIA RTX4090 GPU:
- Hash Rate: 125 million hashes per second
- Time Required to Traverse All Combinations: 1.38 × 10^24 years
This timespan dramatically exceeds not just human civilization, but the estimated age of the universe itself.
Addressing the “Lucky Hit”
Hypothesis Some might argue, “I don’t need to find all combinations; I just need to hit one profitable wallet.” Let’s examine this hypothesis mathematically:
Current Ethereum Ecosystem:
- Total Existing Addresses: 273 million
- Proportion of Total Possible Combinations: Merely 1/5 × 10^32
Calculation of Address Discovery Time:
- Estimated Time to Collide with an Existing Address: 1.27 × 10^17 years
These numbers conclusively demonstrate the impracticality of randomly generating a wallet with existing assets.
Nuanced Security Considerations
Despite the astronomical odds against random generation, cryptocurrency security isn’t an absolute guarantee. Several scenarios could potentially compromise wallet security:
Scenario 1: Partial Mnemonic Phrase Exposure
If 8 out of 12 words in a mnemonic phrase become known:
- Using a single RTX4090 GPU
- Potential to calculate remaining 4 words
- Estimated Cracking Time: Approximately 30 days
Scenario 2: Random Number Generator Vulnerabilities
The fundamental security of cryptocurrency wallets hinges critically on the quality of random number generation. Vulnerabilities in this process can significantly reduce the effective range of generated mnemonic phrases.
Deep Dive: Mnemonic Phrase Generation Mechanism
The process of generating a 12-word mnemonic phrase is a meticulously structured procedure:
1. Initial Random Number Generation
- Computer generates a 128-bit binary number (A)
2. Hash Calculation and Augmentation
- Perform hash calculation on A
- Append first 4 bits of hash result to A
- Result: 132-bit binary number (B)
3. Segmentation and Conversion
- Divide B into 12 groups of 11-bit binary numbers
- Convert each group to decimal
- Match decimal values with corresponding words in mnemonic word list
4. Mnemonic Phrase Compilation
- Assembled 12 words form the complete mnemonic phrase
The Critical Role of Random Number Generation
Random Number Generator Taxonomy:
1. Pseudo-Random Number Generators (PRNG)
- Generated via deterministic algorithms
- Require initial seed value
- Predictable if seed is known
- Quick generation process
- Same seed produces identical number sequence
2. True Random Number Generators (TRNG)
- Leverage unpredictable physical phenomena
- Sources include:
- Weather conditions
- Mobile device accelerometer values
- Radioactive material beta particle emissions
- Typically combine multiple physical data sources
- Mitigate single-point-of-failure risks
Wallet Implementation
Insights Software wallets predominantly employ pseudo-random generators with high-entropy seeds. While providing relatively robust security, they inherently possess subtle vulnerabilities:
- Seed dependency
- Potential periodic cycle patterns
- Theoretical predictability with sufficient computational resources
Real-World Vulnerability
Example In 2023, TrustWallet publicly disclosed a critical security issue:
- Utilized MT19937 pseudo-random number generator
- Potential risk of generating identical mnemonic phrases
- Recommended user asset transfer and version update
Advanced Security Approaches
For security-obsessed users, even hardware wallet True Random Number Generators might feel insufficient. Innovative solutions have emerged:
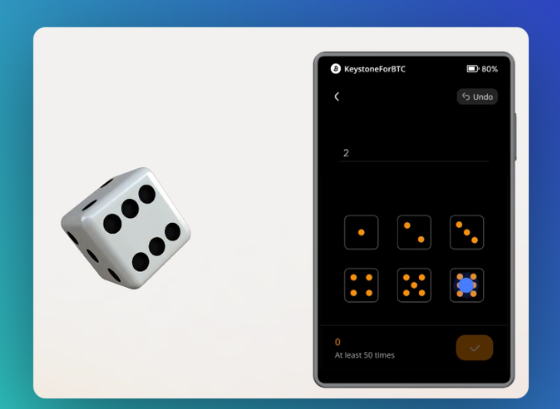
Keystone’s Dice-Based Mnemonic Generation:
- Requires casino-grade dice
- Transparent and evenly weighted
- Minimum 50 dice rolls (99+ recommended)
- Manual input of each roll
- Generates mnemonic phrase through physical randomness
Philosophical Underpinning: “Don’t Trust, Verify”
This approach embodies blockchain’s core principle of personal asset sovereignty, empowering users to directly participate in their security generation process.
Conclusion
While generating a cryptocurrency wallet might seem like a simple task, the underlying mathematical and computational complexities are profound. The cryptographic mechanisms protecting digital assets represent a sophisticated interplay of mathematics, physics, and computer science, designed to provide robust security in an increasingly digital financial landscape.