The new variant of UpdateAgent malware is also capable of dropping adware against macOS.
The IT security researchers at Microsoft Security Intelligence have discovered a new variant of UpdateAgent (aka WizardUpdate) malware targeting Mac devices. UpdateAgent was originally discovered in November 2020 targeting macOS.
New variant, new capabilities, new adware
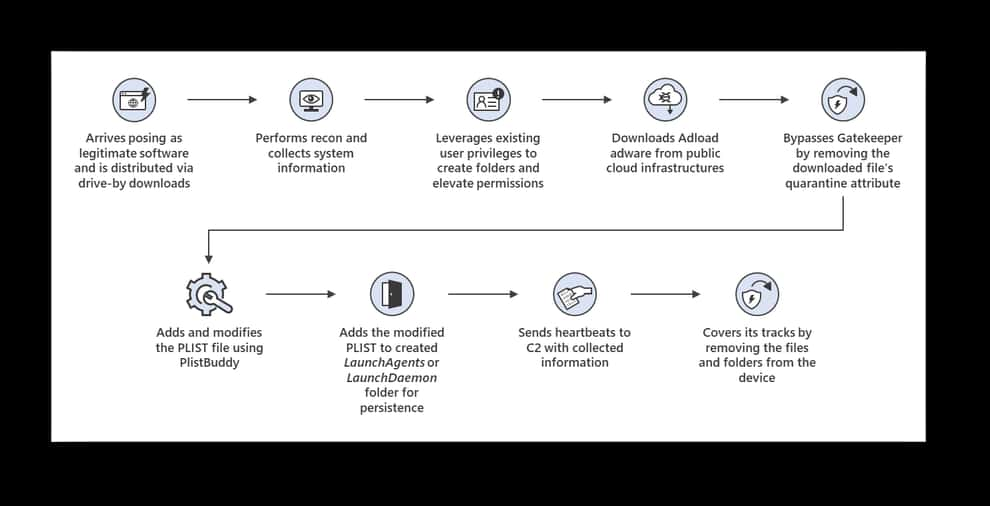
In a series of tweets, Microsoft explained that the variant is equipped with new capabilities including increased persistence and evasion tactics. This indicates that the malware is not only difficult to detect but also hard to get rid of.
Another malicious capability of the malware includes the abuse of public cloud infrastructure to host additional payloads. For instance, upon infection, UpdateAgent installs new adware called Adload.
According to researchers, although, the malware collects and sends system information to a C2 server, one of the most notable additions to the malware’s capabilities is its ability to bypass Apple’s Gatekeeper security feature. It does so by removing the downloaded file’s quarantine attributes.
The screenshot below shows the evolution of Trojan:MacOS/UpdateAgent.B (aka WizardUpdate):
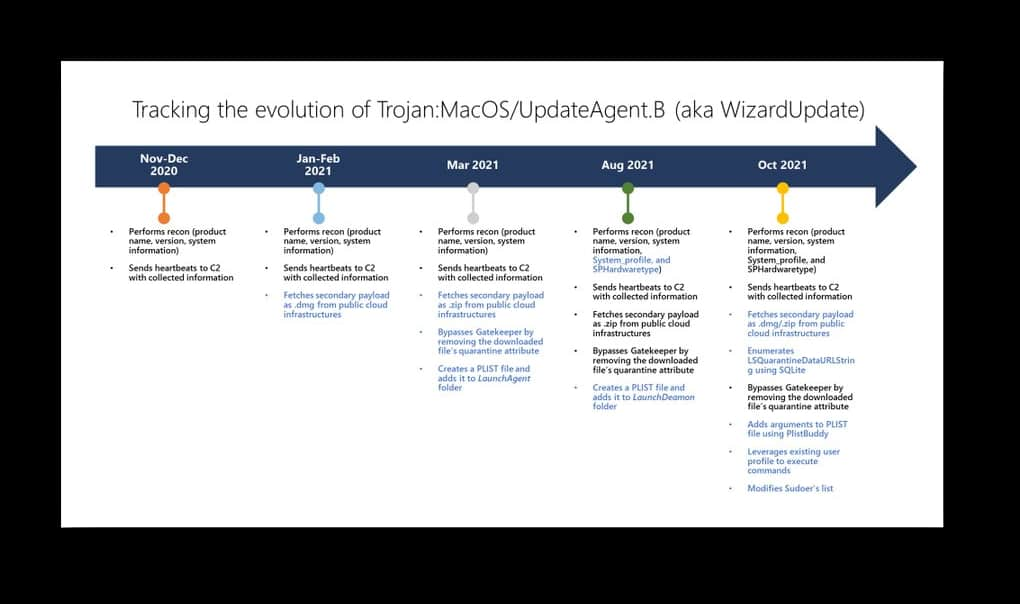
Evolution of Trojan:MacOS/UpdateAgent.B (aka WizardUpdate):
For your information, Gatekeeper is the backbone of macOS’ security as it verifies downloaded applications and enforces code signing before allowing them to run on Macbooks. This reduces the possibility of malware execution.
However, like OSX/Dok malware, UpdateAgent also bypasses the Gatekeeper security feature making it a persistent threat.
The malware also leverages existing user permissions to create folders on the affected device. It uses PlistBuddy to create and modify Plists in LaunchAgent/LaunchDeamon for persistence. It then covers its tracks by deleting created folders, files, and other artifacts, researchers tweeted.
UpdateAgent malware Impersonates legitimate software
The modus operandi of the new variant involves impersonating legitimate software. For now, Microsoft did not reveal precisely which software are being impersonated by the malware. However, the company believes that the new variant is being distributed via drive-by downloads.
A drive-by download attack refers to the unintentional download of malware or malicious code by users on their computers. Simply put: Software downloaded with the user’s permission without understanding its consequences (virus mimicking gaming mods for example) is called a drive-by download.
How to protect your Mac devices from cyber attacks?
Most software for macOS are paid therefore it is easy to lure unsuspecting users into downloading malicious software by impersonating legitimate ones. That is why it is important to refrain from downloading pirated programs or software from third-party websites/marketplaces.
Nevertheless, since Mac devices are constantly under cyber attacks it is vital that users master the art of protecting their devices. Here are some simple tips to follow:
- Use a VPN software
- Disable Remote Login
- Use Two built-in firewalls
- Disable Automatic user login
- Update your Mac OS X regularly
- Install reliable Mac Anti-Virus software
- Set GateKeeper to prevent digitally unsigned apps
- Turn off Java and auto-download in Safari browser.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.
Credit: Source link